 https://www.ikarussecurity.com/wp-content/uploads/2025/03/IMG_2888-1200.jpg
900
1200
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2025/02/IKARUS-Security-Software-4-1.png
IKARUS2025-03-27 13:29:322025-03-27 13:29:33IKARUS Supports HTL Project FENRIR as Partner and Sponsor
https://www.ikarussecurity.com/wp-content/uploads/2025/03/IMG_2888-1200.jpg
900
1200
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2025/02/IKARUS-Security-Software-4-1.png
IKARUS2025-03-27 13:29:322025-03-27 13:29:33IKARUS Supports HTL Project FENRIR as Partner and Sponsor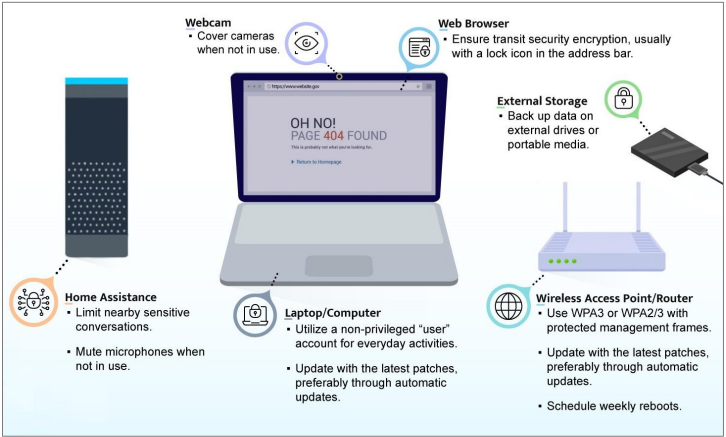
Best practice examples from the NSA Guide to Secure Home Networks (©NSA)
Home network security can affect corporate security through scenarios such as home office or BYOD. The NSA’s new guide to a secure home network helps individuals and admins securely set up and use IT and IoT devices in the home.
New NSA cybersecurity paper for securing home networks
Not only corporate networks, but also private networks are an attractive target for cyber-attacks. Compared to business environments, which are usually professionally secured and managed, they often have fewer security precautions. This is where the new NSA guide [1] comes in, which is particularly suitable for home offices and small offices and is intended to promote security-conscious behaviour, secure configuration guidelines and suitable defence measures.
Best practices for device security
Besides computers, laptops, smartphones, tablets, printers and security cameras, don not forget about IoT applications such as household appliances, assistants or cars. Baby cameras, home monitoring systems, video or game consoles also have access to the internet, cameras and microphones.
- The latest software and operating system versions are more secure than their predecessors are—so upgrade and update them regularly. If possible, set up automatic updates or download patches and updates monthly from a trusted provider.
- To keep routing devices up to date and as secure as possible. It may be useful to use a private router that connects to the router/modem provided by the internet provider. Replace it at the end of the lifetime cycle. Set up a separate guest WLAN for guests.
- Use WAP3 or WAP2/3 to secure your WLAN and use strong passwords with at least 20 characters. Give the default SSID (Service Set Identifier) a unique name. Hiding does not add security, but can cause compatibility problems.
- Network segmentation implements an extra layer of security in your wireless network. At the very least, separate your private WLAN, guest WLAN and IoT network to prevent direct communication between potentially insecure devices.
- Your router should support basic firewall capabilities, including Network Address Translation (NAT) to prevent internal systems from being scanned across the network boundary. If your provider supports IPv6, make sure your router supports IPv6 firewall capabilities.
- Use security software where possible—as part of the operating system or as an additional program—against malware and phishing, as well as for secure surfing and firewall functions. EDR software detects and prevents the execution of malware and can help secure intrusion points through IoT devices. Especially on mobile devices, implement full hard disk encryption to prevent data access in case of loss or theft.
- Use strong passwords and security questions that are difficult to guess and unique to each account. Do not store them in plain text on your system. A password manager can be very helpful to generate and manage strong passwords.
- The administrator account can overwrite all data and settings on your system thanks to its permissions. If malware is executed while you are logged in with an administrator account, it can use these rights for itself. Therefore, use admin accounts only for maintenance, installations and updates.
- Remember that smart assistants and smart devices are constantly listening, even if you are not actively interacting with them. Compromised devices may therefore give attackers direct access to your cameras or microphones. Consider this risk when you are near baby monitors, toys with audio recordings, home assistants and the like. Cover cameras when you are not using them and disconnect devices that are not in constant use from the internet—and update them when you put them back into operation!
- Establish secure user habits: Make regular data backups and store them separately. Charge mobile devices from the wall socket rather than from the computer. Let computers download and install updates automatically when they are not in use. Reboot devices regularly to apply updates. Turn off devices or disconnect them from the internet when they are not in use for a longer period.
- Limit administration to internal network only by disabling the ability to make remote changes from the router and disabling Universal Plug-n-Play (UPnP). This way you close possible security gaps that can be used by attackers.
- Reboot your devices incl. routers regularly—at least weekly—to reduce the dangers from non-persistent threats. Reboots help to remove non-persistent infections that have been observed especially in home routers.
- The security of your devices at home can have a direct impact on the security of your company data and networks. For teleworking, use a VPN (Virtual Private Network) as one security measure. Ensure secure connections and strong encryption for collaboration tools, ideally end-to-end.
Best practices for online behaviour
There are many dangers when using the internet on a daily basis – from phishing attacks to malware ads, unsafe applications or infected attachments or downloads. The following recommendations from the NSA guide for secure home networks are based on best practice examples for secure browsing and communication.
- Emails are popular attack vectors, so be especially careful when dealing with unexpected messages, links or attachments. If necessary, verify authenticity via an alternative channel such as a phone call. Use strong, unique passwords, avoid out-of-office notes and use secure email protocols, TLS and encryption (Secure IMAP, Secure POP3).
- Modern, updated browsers are better able to alert users to missing or disabled security features. Also, look for the lock icon for secure content transfer.
- Use social media wisely and do not post any personal data that can be used for attacks or allow conclusions to be drawn about your security questions. Limit your contacts, verify them outside of social media and never click on unexpected links. Watch out for fake profiles and check the platform’s security policy and your security settings once a quarter and when the terms of use change.
- Make sure you have secure authentication measures on your router. Use a password manager rather than the remember functions of browsers and programs. Enable multi-factor authentication wherever possible, ideally one of the more secure app- or device-based variants.
- Avoid public Wi-Fi networks whose security status you do not know, and instead use your mobile network (i.e. mobile Wi-Fi, 4G or 5G services) or company or private hotspots with strong authentication and encryption. If you must use a public network, use a trusted VPN and do not leave your device unattended.
- Separate professional and private content by using different hardware and accounts and not sharing data between private and professional accounts. It is safer to access data remotely than to send copies. Use special security software for private devices in the company environment (BYOD). Always use a VPN or other secure channel, regardless of the device, to ensure that all data is protected by encryption.
- Use different devices for different activities and confidentiality levels, so that, for example, financial transactions or authentication always take place on a different device than entertainment and games.
This might also interest you:
Tips for secure online gaming
Tips to better secure smart home devices
Securely erasing data

















