 https://www.ikarussecurity.com/wp-content/uploads/2025/12/Attack-Surface-Management-600.jpg
467
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2025/02/IKARUS-Security-Software-4-1.png
IKARUS2025-12-09 11:49:312025-12-09 11:49:32Attack Surface Management (ASM)
https://www.ikarussecurity.com/wp-content/uploads/2025/12/Attack-Surface-Management-600.jpg
467
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2025/02/IKARUS-Security-Software-4-1.png
IKARUS2025-12-09 11:49:312025-12-09 11:49:32Attack Surface Management (ASM)Cyberattacks on infrastructure, production and supply systems are a real threat that can affect us all, especially in times of crisis. “Due to the global Covid19 crisis, computer systems were made accessible for remote working quite pragmatically in a relatively short period of time,” warns Herbert Dirnberger, Industrial Cyber Security Expert at IKARUS: “Industrial control systems could also be too easily accessible via the internet at the moment.“
Operational Technology (OT) is a distinct category of computer and communication systems used to manage, monitor and control industrial operations. IoT security means the protection and control of “intelligent” devices that are integrated into operational networks.
OT security in practice: between best practice and rookie mistakes
In a water treatment plant in Florida/USA, an increased amount of acid was released into the general water supply system at the beginning of 2021 due to the manipulation of control systems. The disturbance was detected in time, and no one was injured. However, it gives food for thought – not least because it demonstrates that technically sophisticated attacks can be successful. Still, security in OT can fail due to negligence, lack of compliance or human error.[1] That an attack would be fatal does not automatically lead to more robust measures.
Many of the attacks are not targeted and very often hit production companies that do not take the issue seriously enough”, says Herbert Dirnberger. Awareness of the need for OT protection measures has grown considerably in recent years. Now words must be followed by action, and the first concrete steps must be taken: “It has to work together to make such cyber Security incidents may occur. Often it is due to non-existent specifications, lack of security measures, incorrectly functioning technology and the time factor.“
Defence in Depth: OT security sensibly planned and lived
The development of OT security is moving towards the standardization of security requirements. The Defense in Depth protection concept is an essential component of standards such as IEC 62 443, which are now applied as a reasonable practice in critical infrastructure, production processes, logistics and other operational processes of OT. Security is rolled out in three layers.
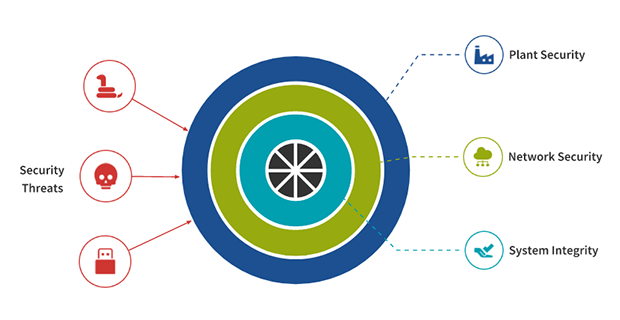
Figure 1: Defense in Depth: A multi-layer concept for safeguarding industrial plants (© Herbert Dirnberger)
Plant Security includes facility-wide measures such as security policies and physical protection of equipment.
Network security includes secure communication within the facility and via remote access, as well as Mirco segmentation of the network area with firewalls.
System Integrity describes operational measures and levers such as system hardening, patch capability, malware protection, access control and user management, security logging and monitoring, and backup and restore.
A significant challenge of the Defense in Depth concept is that it cannot be implemented by the system owner alone. All stakeholders who introduce potential vulnerabilities into the overall system must play their part: operators, service providers and system integrators close gateways through password and account mismanagement. Product suppliers prevent hard-coded passwords and elevation of privileges.
Without clear guidelines, control and awareness, it does not work
A practical example is the four-eye principle, which is also applicable to remote access services: “Secure remote maintenance takes place exclusively on-demand from the operating team and always under at least four eyes”, says Herbert Dirnberger: “The VPN access is only open when it is needed and is also secured with 2-factor authentication. In addition, all relevant actions are logged in.” In addition, all relevant actions are logged as well.” The first (!) step towards a secure OT environment is risk assessment. Depending on the size and structure of the company, this is easier said than done: In grown systems, it becomes a mammoth task to identify and document all – and not only supposedly relevant – assets. Only when all systems, devices and protocols are visible can the risk analysis begin.
„With technology partner Nozomi Network, we help operators to obtain the necessary transparency about the entire IT/OT network, including vulnerabilities, and support them in setting up the Defense in Depth protection concept,” says Herbert Dirnberger: “A particularly unique selling point of Nozomi Guardian is the ability to record process variables and trigger alarms in the event of deviations. This valuable feature of the Nozomi OT-Security Sensor brings complete transparency to the production process, as every change can be traced.“
With IKARUS, you use the partner technologies and threat intelligence of Nozomi Networks and FireEye with local data processing in the IKARUS data centre in Vienna. As a local system integrator, central point of contact and technical support team, we also actively advise and accompany you in setting up and merging IT and OT security and enable complete onboarding within just four weeks.
Get advice now:
Mail: sales@ikarus.at
Phone: +43 1 58995-500
Information on IT, OT and IoT security
Worth reading:


















