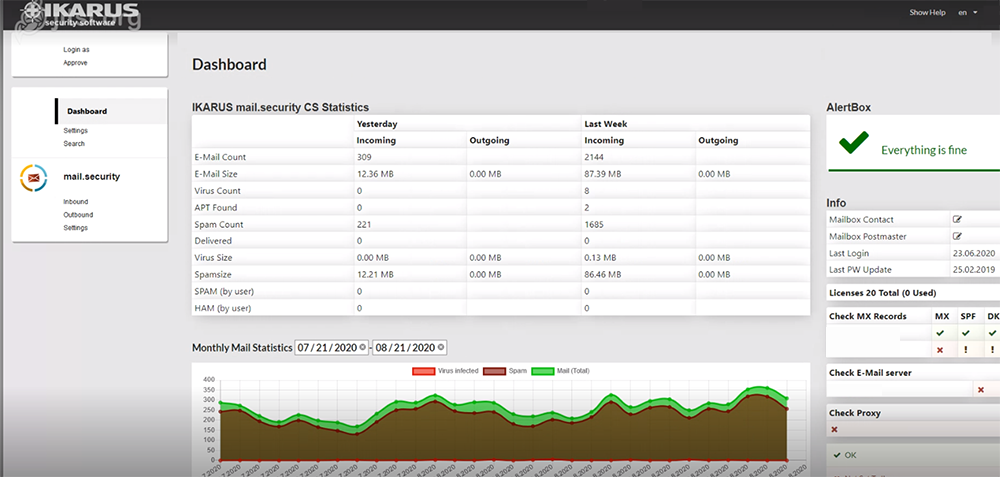
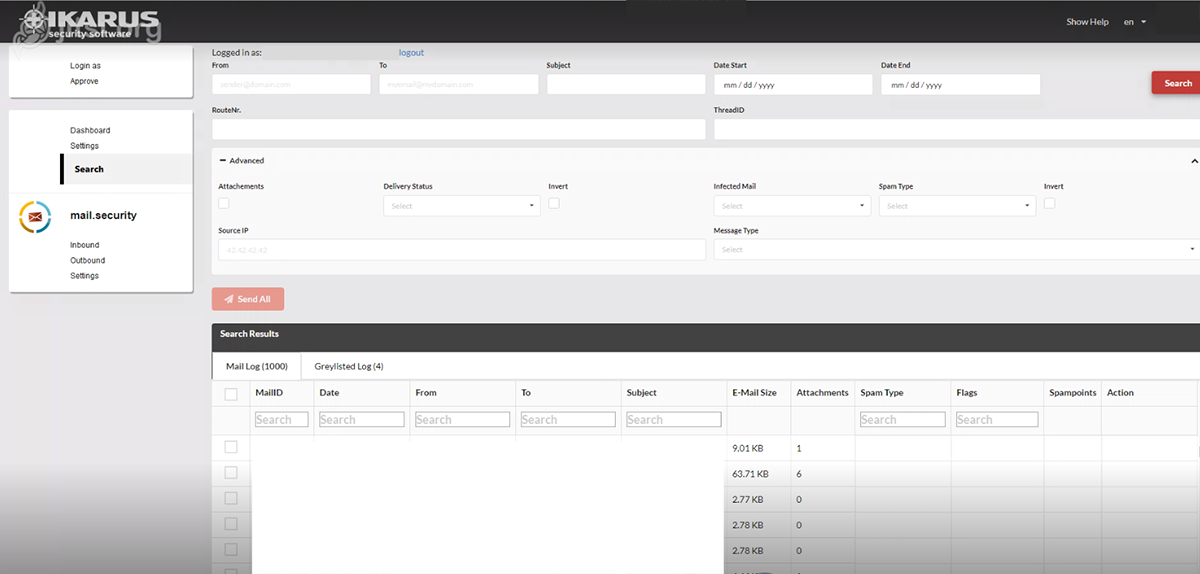
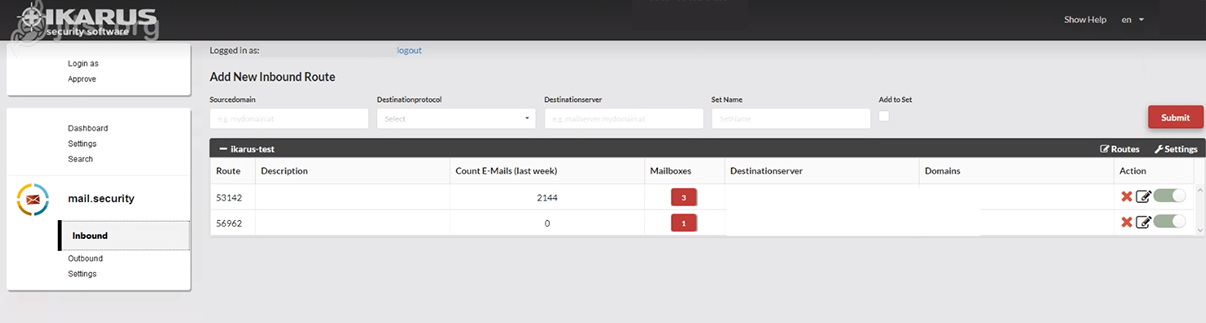
Dashboard
The new dashboard contains all of the known data from the previous IKARUS interface. It provides an overview of the entire account or all activated IKARUS services.
The summary shows statistics on:
- IKARUS mail.security (with/without APT protection)
- IKARUS web.security
- IKARUS wifi.security
Dashboard – Search
An advanced email search and the grey list log are combined in one search. Search criteria that are already known, such as delivery status or virus infections, are also included.
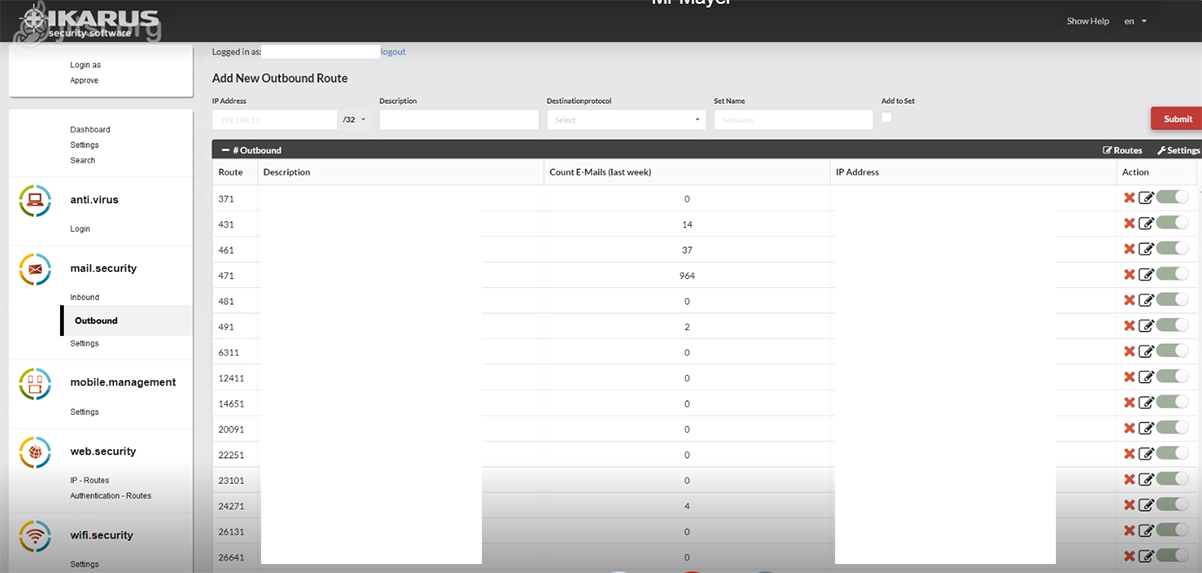
IKARUS mail.security – Inbound or Outbound
This is where you can request new routes or edit existing routes. Click on “Settings” to access the settings of the respective set.
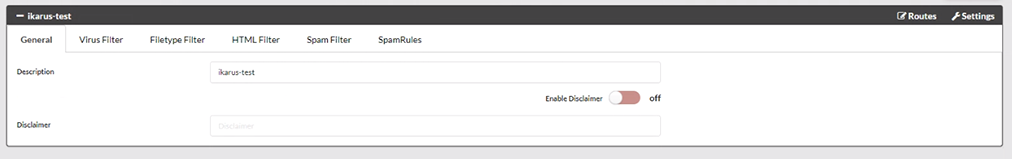
IKARUS mail.security – General
This is where you can configure a disclaimer.
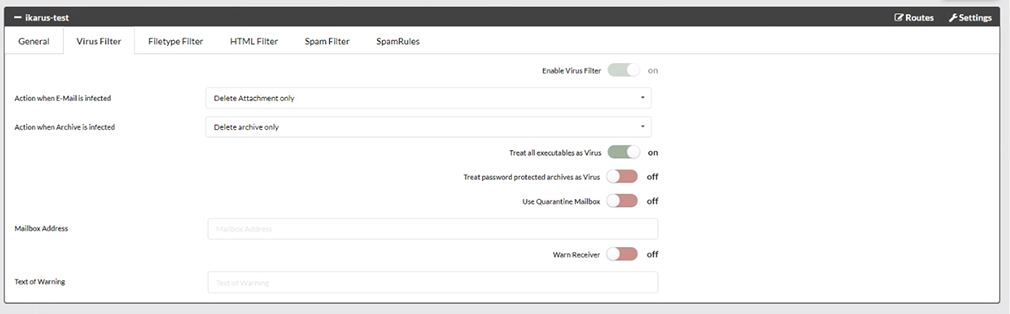
IKARUS mail.security – Virus Filter
This is where you can define what is to happen when a virus is found and how password-protected archives should be dealt with.
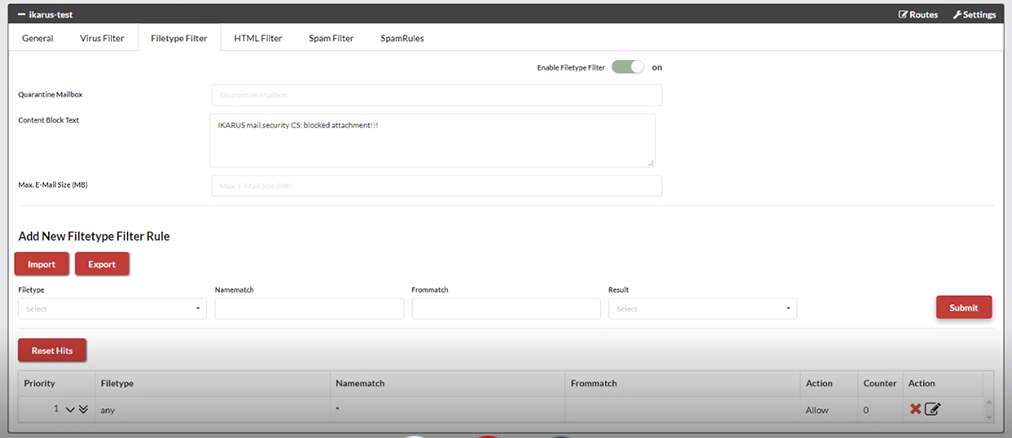
IKARUS mail.security – Filetype Filter
This is where you can block certain file types, for example on the basis of the sender. If you want this to apply to all senders, enter an “*” as a placeholder.
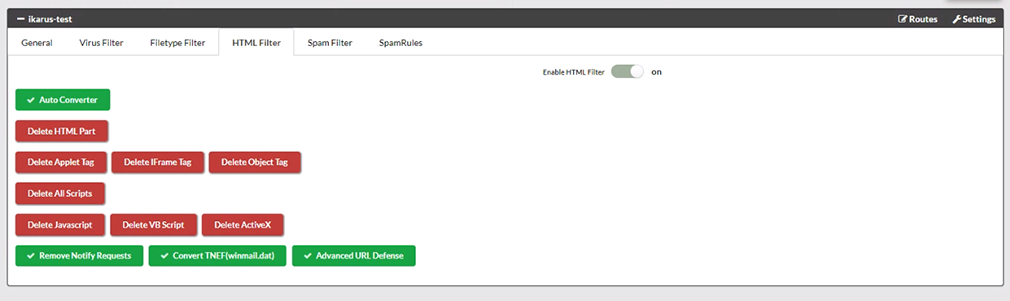
IKARUS mail.security – HTML-Filter
The HTML filters build on each other. The auto conversion turns a pure HTML e-mail into an e-mail consisting of HTML and text.
“Remove HTML”: Deletes any HTML part from the email. To remove only certain parts, distinguish between tags that should be deleted and scripts. It is also possible to remove all scripts.
“Remove Notify Requests” removes read and receipt confirmations from emails.
“Convert TNEF” converts winmail.dat files back to standard emails.
“Advanced URL Defense” scans links not only when an email is received, but again each time the URL is clicked. This means that even delayed attacks are detected and blocked.
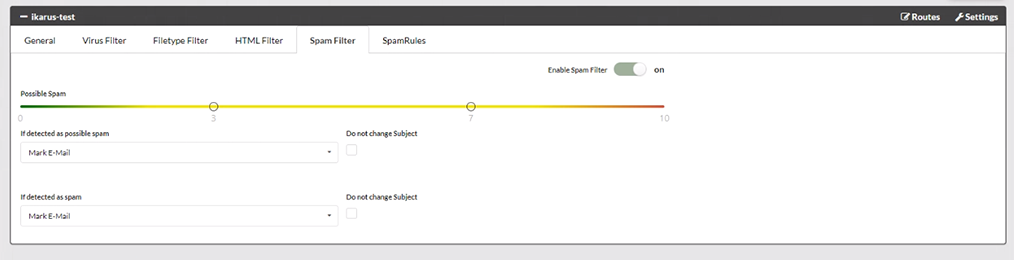
IKARUS mail.security – Spam Filter
Each e-mail message checked by IKARUS passes through numerous filters and is evaluated according to various criteria (e.g. SPF, dynamic word filter, rules, etc.). The more minus points allocated to an e-mail, the higher the probability that it is ‘true spam’. You can use the slider to define the level of sensitivity of IKARUS mail.security when it reacts.
The slider shows the threshold values for ‘possible spam’. The actions that should be taken for spam or possible spam can be set below.
The example in the screenshot shows the following settings:
0 points to 3 points: everything in order, no spam, no marking of emails
3 points to 7 points: possible spam
7 points to 10 points and higher: spam
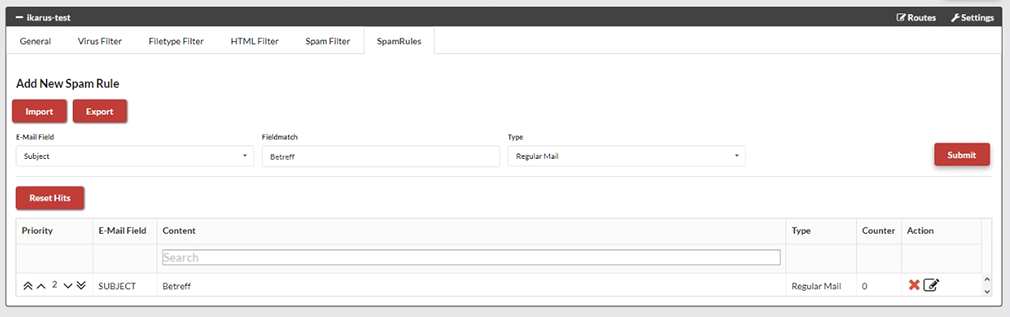
IKARUS mail.security – Spam Rules
Rules can be defined to categorise emails: for example, if a sender is on multiple blacklists but the user wants to continue receiving emails until the clean-up is complete.
E-mail log: This is where you define what the filter should focus on.
Sender: This is the actual sender (the ‘envelope sender’) of the e-mail, but this does not necessarily correspond to the sender identified in the e-mail programme.
Recipient: This shows to whom the e-mail was sent. This is also where you can select a single address that will be excluded from the spam filter.
Subject: This is where you can identify a specific part of the text that is part of the subject.
Text: This is where a specific text sequence can be identified, which can be found in the main part of the e-mail.
Content: This is where you can find the content. It identifies the character string used to perform a search for sender, recipient, subject or text. It should be noted that the search is performed only for the string, without taking into account what comes before or after it. For example, if a search is made for the text “count”, the word “accounting” is included in the search result.
Input: This determines what happens to an email when it is selected by the spam filter. The possible selections that could be made are regular, possible or spam.
Counter: This is where you can count how often the rule has been applied since it was implemented. The counter can be reset for all rules using the function “Reset all counters”.
Action Rules can be deleted, edited, moved up or down. It should be noted that the rules are processed from top to bottom, using the first applicable rule. This means that the order of the rules is relevant.
IKARUS mail.security – Outbound
The settings for outgoing routes (‘outbound’) are identical to those settings for incoming routes as described above.
Under outgoing you will find the detailed settings for the disclaimer and what actions have been requested if a threat is found in an email.
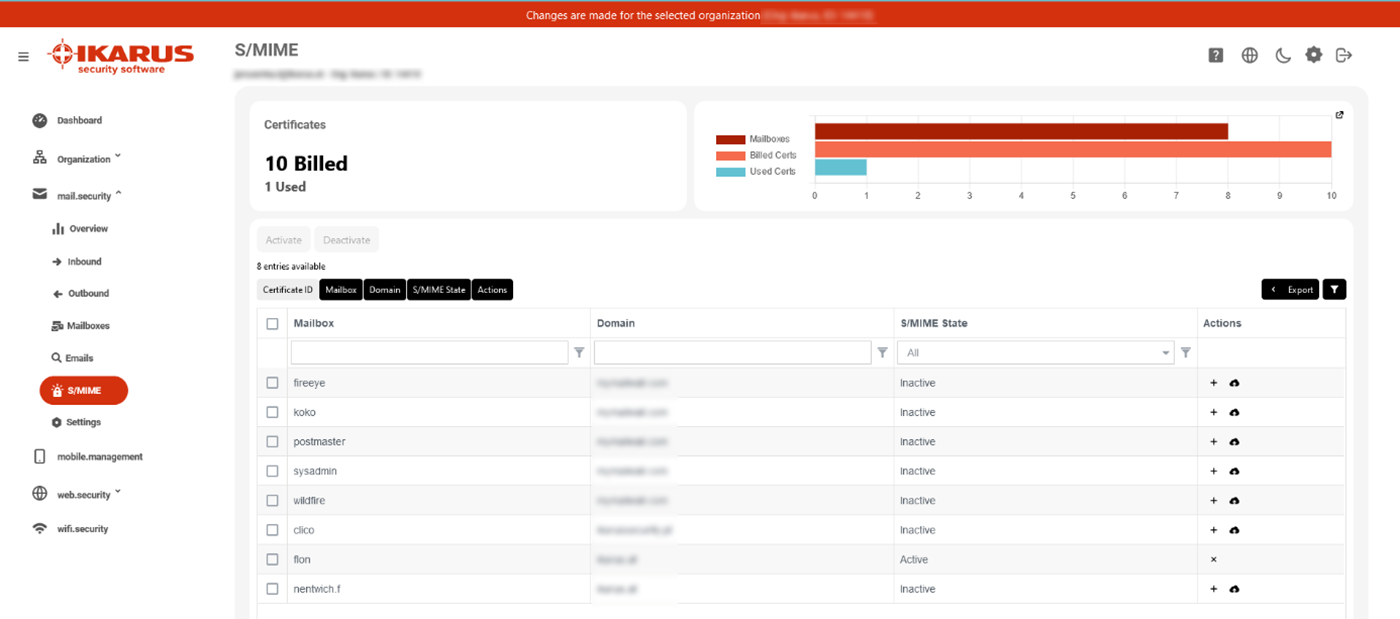
IKARUS mail.security – S/MIME
As soon as the S/MIME feature is licensed for you, you have the option here to select from all created mailboxes for which you want to request a certificate. All outgoing e-mails of an active mailbox are automatically signed when sent via IKARUS mail.security.
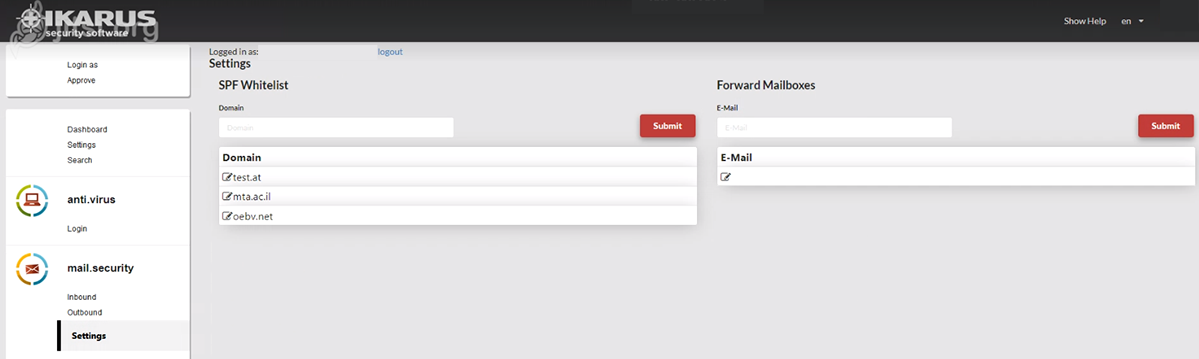
IKARUS mail.security – Settings
This is where you can activate an SPF whitelist and an email address for forwarding.
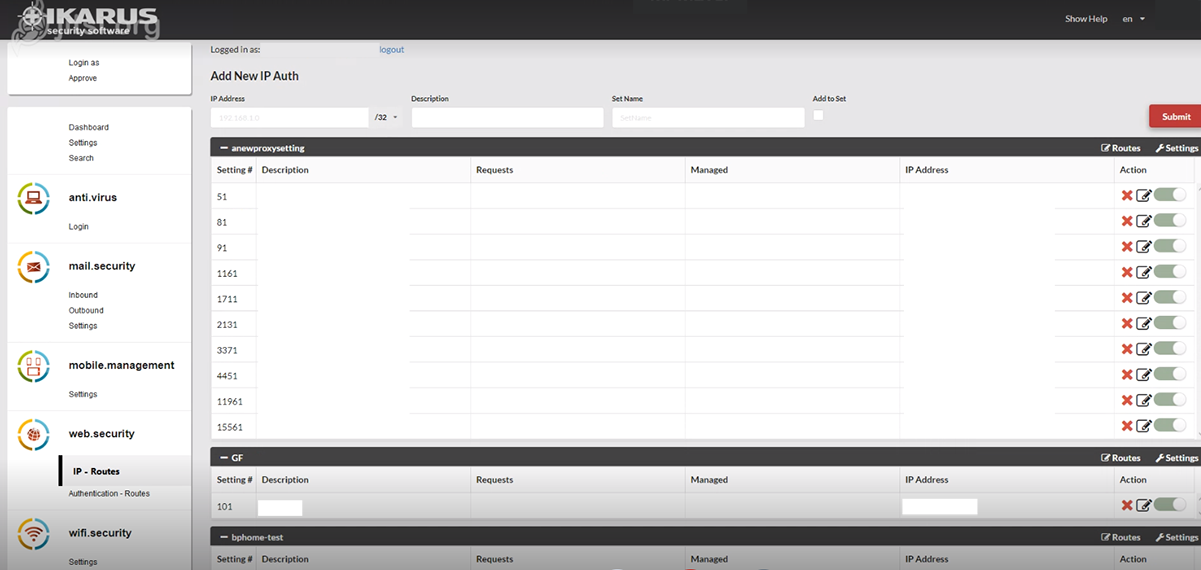
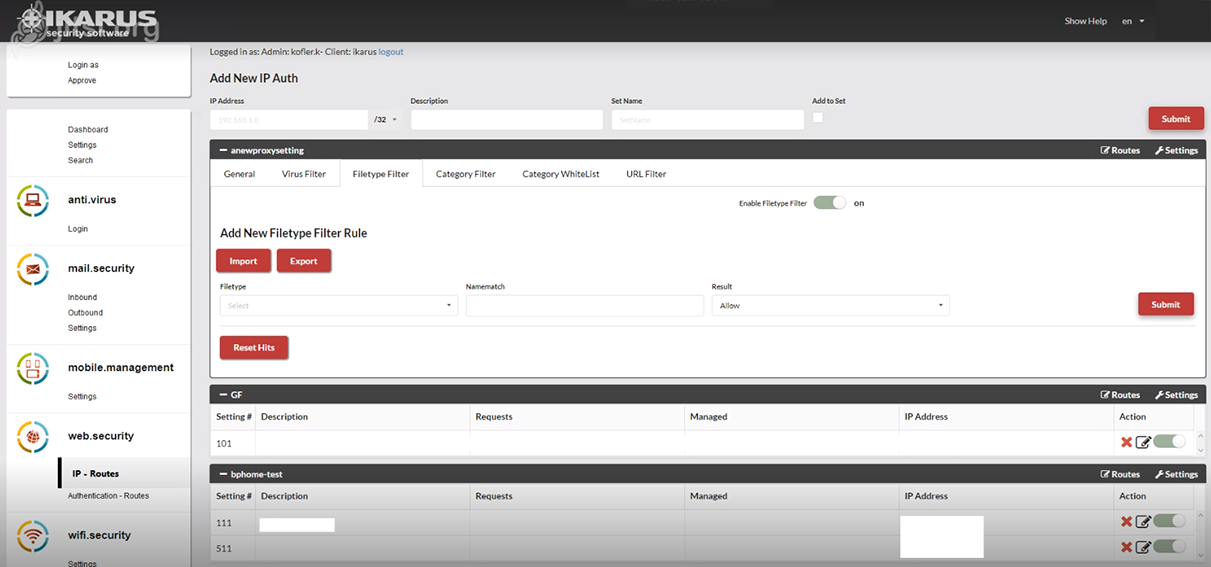
IKARUS web.security – IP – Routes
This is also where new IP routes can be applied for IKARUS and existing routes can be changed.
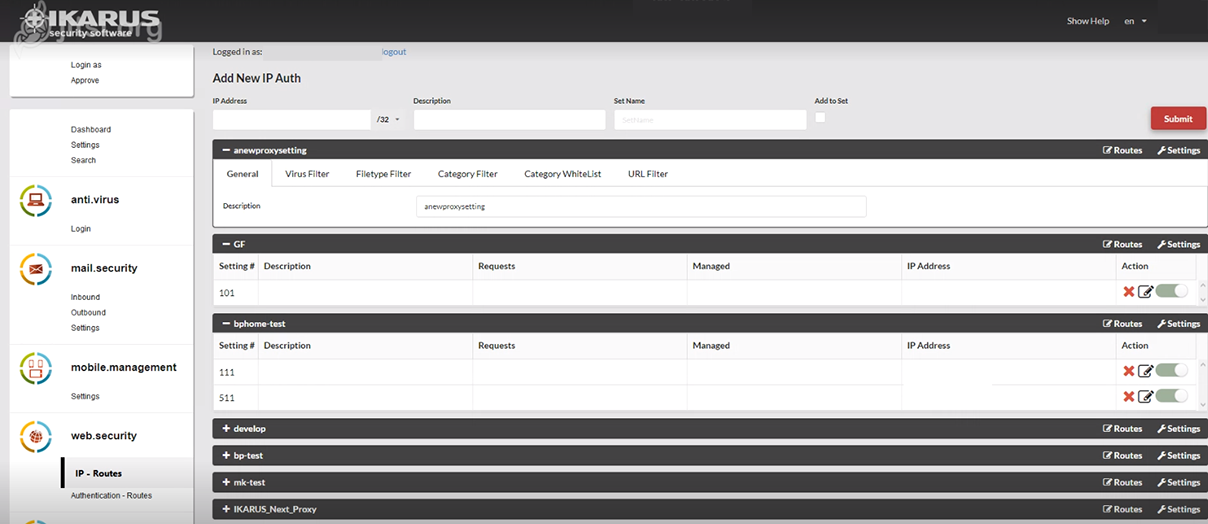
IKARUS web.security – Settings
Several routes are combined to form a “set”. This is where you can describe the sets.
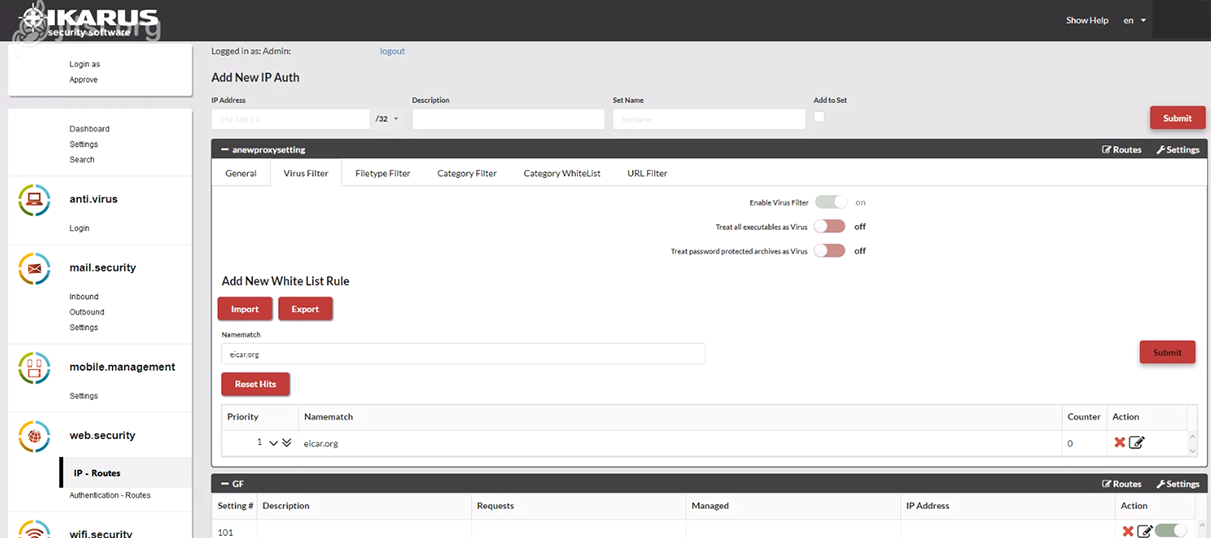
IKARUS web.security – Virus Filter
This is where you can decide what is to happen when a virus is found and how password-protected archives should be dealt with. You can also assign rules for a white list.
.
IKARUS web.security – Filetype Filter
This is where you can define what should happen to certain file types.
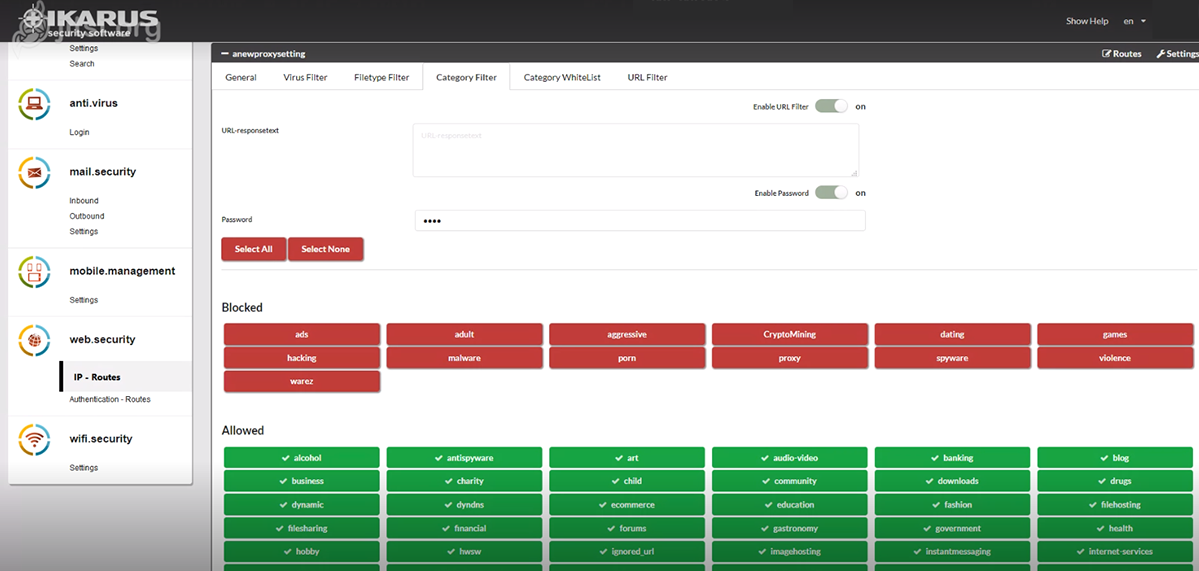
IKARUS web.security – Category Filter
This is where you have the option to block categories that are already predefined (according to international guidelines).
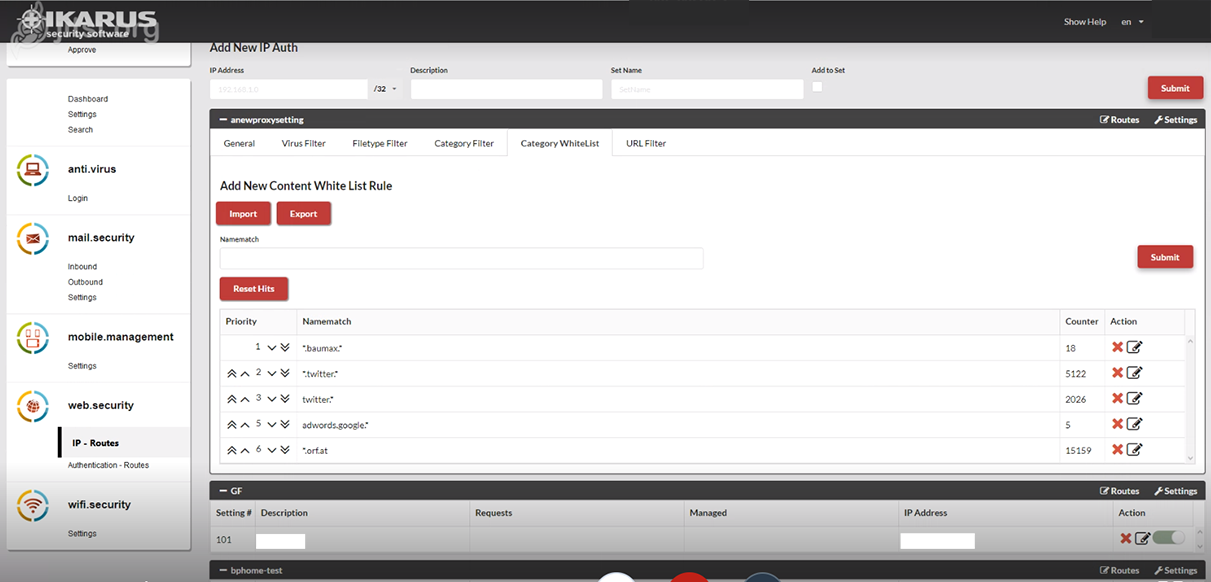
IKARUS web.security – Category White List
This is where you can allow selected categories (“white list”).
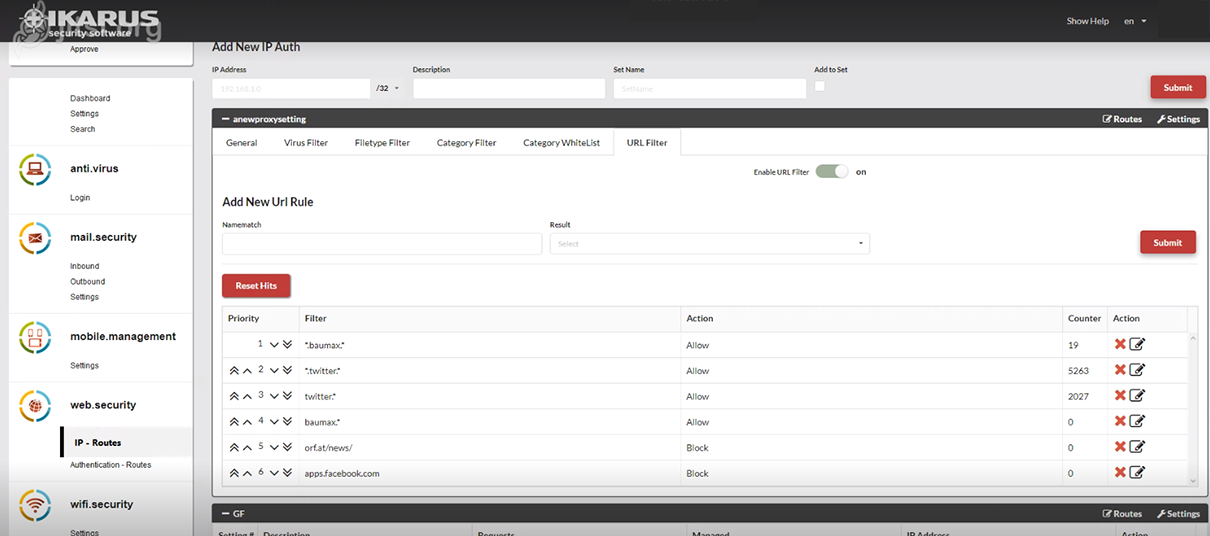
IKARUS web.security – URL-Filter
This is where you can allow or forbid certain URLs.
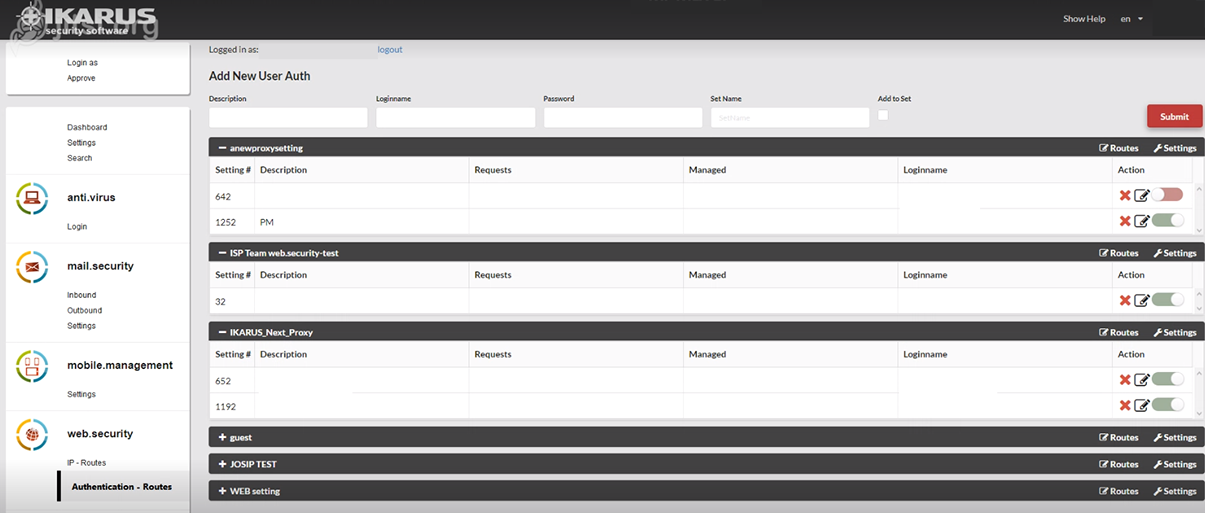
IKARUS web.security – Authentication – Routes
This is where you can assign a username and password for the dial-in to the proxy service. The setting options correspond to those of the “IP Routes” as described above.
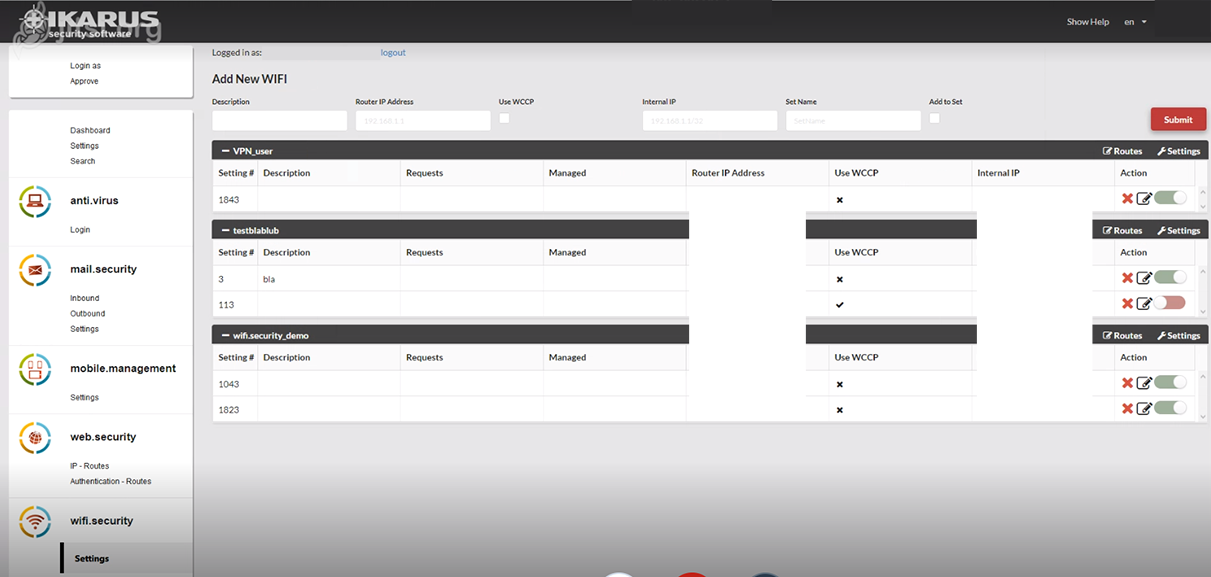
IKARUS wifi.security
This is where you can manage the Wi-Fi routes. All other setting options are identical to those of IKARUS web.security as described above.