 https://www.ikarussecurity.com/wp-content/uploads/2025/12/Attack-Surface-Management-600.jpg
467
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2025/02/IKARUS-Security-Software-4-1.png
IKARUS2025-12-09 11:49:312025-12-09 11:49:32Attack Surface Management (ASM)
https://www.ikarussecurity.com/wp-content/uploads/2025/12/Attack-Surface-Management-600.jpg
467
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2025/02/IKARUS-Security-Software-4-1.png
IKARUS2025-12-09 11:49:312025-12-09 11:49:32Attack Surface Management (ASM)S/MIME (“Secure/Multipurpose Internet Mail Extensions”) is a standard for the secure signing of e-mails. Outgoing messages are provided with a digital signature which – depending on the variant – proves the sender’s address or identity. Conversely, an intact digital signature and a trustworthy, valid certificate identify incoming messages as authentic. In this way, manipulations of the content or sender name can be detected and unmasked.
Email security in several layers
Even in the age of messenger services, emails are one of the most important means of communication in organisations – especially when it comes to external communication partners. The fact that they offer a direct route into the corporate network and often contain sensitive information makes them particularly worthy of protection.
Complementing the defence against malware, spam and phishing attempts through malware filters, digital signatures can add another layer of security. Using S/MIME certificates, the email client automatically creates digital signatures that can be read by all common email clients. If your e-mail client confirms an intact, valid signature, the authenticity of the sender’s address is considered verified. Non-intact signatures indicate that the sender address has been forged or that the contents of the e-mail have been manipulated. Spear phishing, social engineering and identity theft can thus be unmasked.
How does the S/MIME signature work?
S/MIME uses asymmetric cryptography, i.e. two different keys. The private key generates the respective unique digital signature and the public key can verify it. Signing is usually done automatically, the private key is stored in the software or hardware used. The public key, which can be read by any compatible system, is also automatically sent with the signed e-mail. It is not possible to draw conclusions from the public key to the private key.
The use of SMIME signatures does not change anything for the e-mail sender. However, anyone who receives a signed e-mail will see a small icon near the sender’s name in his or her e-mail programme, which indicates either a valid signature and a valid certificate or problems with the signature or the certificate.
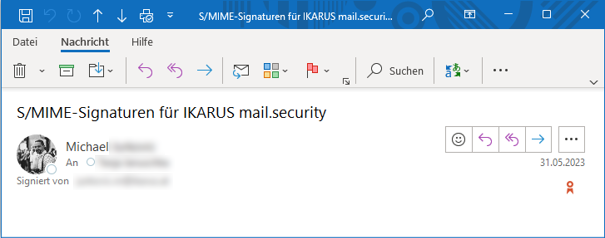
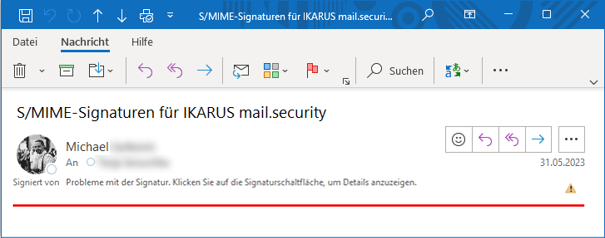
E-mails with a digital signature are marked as valid or invalid with an icon in the e-mail preview and in the e-mail view. Click on the icon to call up further information on the signature and the certificate.
Create and use secure S/MIME certificates
In principle, the use of S/MIME signatures is open to everyone; they can be issued by oneself or obtained from various – also free – providers. The downside of the free offers is their limited usefulness: Security is only provided by certificates that are recognised as trustworthy and are classified as such by the e-mail systems. Even signed or free certificates would have to be manually deposited as trustworthy in the recipient system; for this, the sender and signature would have to be “manually” authenticated beforehand in an alternative way. The benefit for business communication is therefore limited.
Reputable commercial providers prove reliable authentication of their licensees. Their certificates are automatically recognised by common email clients and classified as trustworthy. The digital signature is thus immediately ready for use and functional
.
This might also interest you:
















 Irina Iriser / Pexels.com
Irina Iriser / Pexels.com