https://www.ikarussecurity.com/wp-content/uploads/2024/12/color-teams.png
300
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2023/09/IKARUS-Security-Software-1.png
IKARUS2024-12-13 10:12:112024-12-13 10:12:16Red Teams, Blue Teams, Purple Teaming
https://www.ikarussecurity.com/wp-content/uploads/2024/12/color-teams.png
300
600
IKARUS
https://www.ikarussecurity.com/wp-content/uploads/2023/09/IKARUS-Security-Software-1.png
IKARUS2024-12-13 10:12:112024-12-13 10:12:16Red Teams, Blue Teams, Purple TeamingCybercrime is undergoing rapid change. Attacks adapt, combine and vary zero-day exploits, malware, phishing, man-in-the-middle and denial-of-service attacks as needed. Additionally, actors are constantly adapting to technical and societal developments, acting in a globally networked manner and dynamically changing focus to the most lucrative areas.
Threat Intelligence enables CISOs and IT leaders responsible for production to keep up with the pace of attackers and digitalisation.
Different impacts of cyber-attacks on IT and OT
The collective term Operational Technology (OT) refers to both hardware and software for monitoring and controlling industrial plants, processes and important facilities such as environmental controls or access and monitoring systems. The Industrial Internet of Things (Industrial IoT or IIoT) refers to networked sensors, instruments and smart devices or objects. Industrial IT connects automation networks in industry with IT structures. While incidents involving conventional IT systems usually “only” affect digital data, OT and IoT devices also control and monitor systems in the physical world. The security of critical infrastructures stands and falls with them.
Attacks on OT hardware and software are increasing and evolving rapidly. The business is worthwhile: control systems, process control technology and building automation offer new points of attack through connection to the internet. Most industrial companies already have more network participants in OT than in IT. The impact of OT security incidents ranges from the immediate disruption of processes, such as shutting down a plant, to compromised integrity of industrial environments with the risk of harm to people and resources.
Increase in threat scenarios for OT systems expected
According to analyst firm Gartner, by 2025, cybercriminals will manage to use these operational technology environments in organisations as a weapon to successfully hurt people. [1]
A recent example where production was severely affected is the cyber attack on the Upper Austrian engine manufacturer Rotax in August 2022. [2]
A ransomware attack on the Colonial Pipeline in USA 2021 affected millions of people. The potential impact of insecure OT systems goes a long way. They highlight the priority of properly segmenting and well securing IT and OT networks. Gartner writes: “In operational environments, security and risk management leaders should be more concerned about real world hazards to humans and the environment, rather than information theft.” Gartner identifies three main motivations for security incidents in OT systems: actual damage, commercial vandalism (reduced performance) and reputational damage.
However, risks also exist in internal operations: simple configuration errors, bugs, manual interventions and, above all, poorly coordinated pentretation tests in these environments can lead to security incidents that produce quality losses, production stoppages and unintentional data leaks.
Faster detection and defence of attacks through Threat Intelligence
In the field of cyber security, the more that is known about potential threats, the better prepared one is considered to be. Threat intelligence links multiple sources of information and events. This includes threat types, basic functions, the actions of threat actors, the structure of exploits, malware, vulnerabilities or the key figures of security breaches. [3]
Threat Intelligence uses this overarching evidence-based information on cyber-attacks, which has previously been organised and processed by cybersecurity experts. All data is put into context to enable optimal prevention and rapid response to security incidents. In this way, new patterns become visible, and cyber defence is not limited to purely reactive measures.
The use of threat intelligence also brings convincing advantages in the protection of industrial environments and critical infrastructures: In addition to targeted manipulations, it enables real-time detection and defence against classic threats such as ransomware. Together with the defence-in-depth concept and interactive network visualisation, the real-time detection of threats and anomalies through threat intelligence is one of the best practices in OT security.
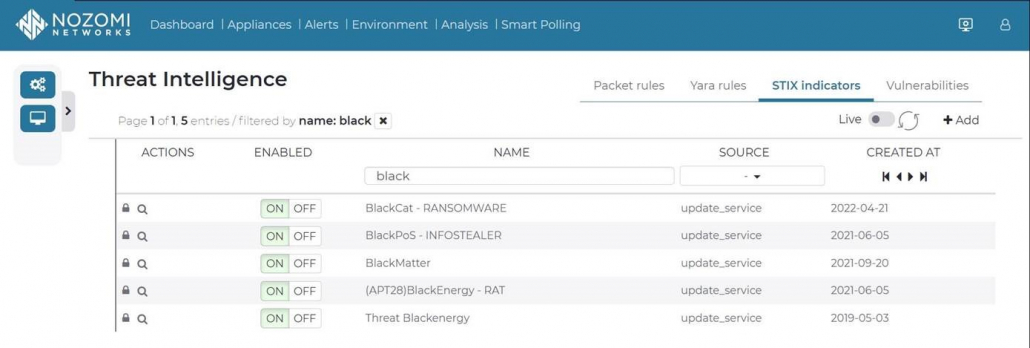
Example of practice – Screenshot Nozomi Guardian: With integrated threat intelligence, Nozomi’s OT security sensors effectively protect against ransomware and other threats.
Learnings and recommendations for OT systems
Threat intelligence can significantly improve the security measures of companies at all levels. Well-prepared and contextualised knowledge about cyber threats, attackers and methodology forms the foundation. This abstracted information enables strong defences as well as proactive prevention measures. Industrial systems and critical infrastructures benefit from up-to-date threat and vulnerability information to detect advanced threats and cyber risks at early and late stages and identify assets at risk of attack through OT and IoT vulnerability assessment.
Reading recommendations:
Defense in Depth: Multi-layer approach for lived OT security
How to protect from the BlackCat Ransomware
Real-time protection against ransomware BlackMatter
Sources: